Emissary-ingress Release Notes
Version 2.0.5
Feature: AuthService circuit breakers
It is now possible to set the
circuit_breakers for AuthServices, exactly the same as for Mappings and TCPMappings. This makes it possible to configure your AuthService to be able to handle more than 1024 concurrent requests.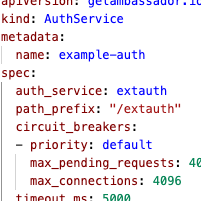

Improved validity checking for error response overrides
Any token delimited by '%' is now validated agains a whitelist of valid Envoy command operators. Any mapping containing an
error_response_overrides section with invalid command operators will be discarded.Bug Fix: mappingSelector is now correctly supported in the Host CRD
The
Host CRD now correctly supports the mappingSelector element, as documented. As a transition aid, selector is a synonym for mappingSelector; a future version of Emissary-ingress will remove the selector element.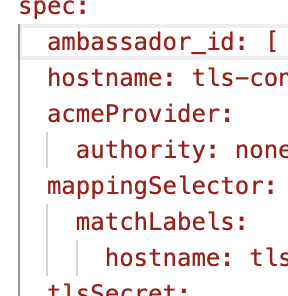

Version 2.0.4 (October 19, 2021)
Feature: General availability!
We're pleased to introduce Emissary-ingress 2.0.4 for general availability! The 2.X family introduces a number of changes to allow Emissary-ingress to more gracefully handle larger installations, reduce global configuration to better handle multitenant or multiorganizational installations, reduce memory footprint, and improve performance. We welcome feedback!! Join us on Slack and let us know what you think.


Change: API version getambassador.io/v3alpha1
The
x.getambassador.io/v3alpha1 API version has become the getambassador.io/v3alpha1 API version. The Ambassador- prefixes from x.getambassador.io/v3alpha1 resources have been removed for ease of migration. Note that getambassador.io/v3alpha1 is the only supported API version for 2.0.4 — full support for getambassador.io/v2 will arrive soon in a later 2.X version.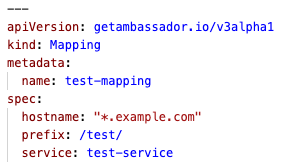

Feature: Support for Kubernetes 1.22
The
getambassador.io/v3alpha1 API version and the published chart and manifests have been updated to support Kubernetes 1.22. Thanks to Mohit Sharma for contributions to this feature!

Feature: Mappings support configuring strict or logical DNS
You can now set
dns_type between strict_dns and logical_dns in a Mapping to configure the Service Discovery Type.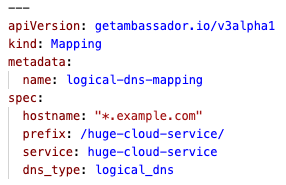

Mappings support controlling DNS refresh with DNS TTL
You can now set
respect_dns_ttl to true to force the DNS refresh rate for a Mapping to be set to the record's TTL obtained from DNS resolution.Support configuring upstream buffer sizes
You can now set
buffer_limit_bytes in the ambassador Module to to change the size of the upstream read and write buffers. The default is 1MiB.Bug Fix: Version number reported correctly
The release now shows its actual released version number, rather than the internal development version number.
Large configurations work correctly with Ambassador Cloud
Large configurations no longer cause Emissary-ingress to be unable to communicate with Ambassador Cloud.
Bug Fix: Listeners correctly support l7Depth
The
l7Depth element of the Listener CRD is properly supported.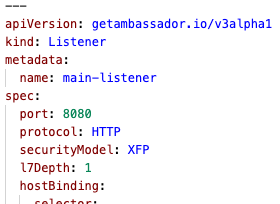

Version 2.0.3-ea (September 16, 2021)
Developer Preview!
We're pleased to introduce Emissary-ingress 2.0.3 as a developer preview. The 2.X family introduces a number of changes to allow Emissary-ingress to more gracefully handle larger installations, reduce global configuration to better handle multitenant or multiorganizational installations, reduce memory footprint, and improve performance. We welcome feedback!! Join us on Slack and let us know what you think.
AES_LOG_LEVEL more widely effective
The environment variable
AES_LOG_LEVEL now also sets the log level for the diagd logger.AmbassadorMapping supports setting the DNS type
You can now set
dns_type in the AmbassadorMapping to configure how Envoy will use the DNS for the service.Building Emissary no longer requires setting DOCKER_BUILDKIT
It is no longer necessary to set
DOCKER_BUILDKIT=0 when building Emissary. A future change will fully support BuildKit.Version 2.0.2-ea (August 24, 2021)
Developer Preview!
We're pleased to introduce Emissary-ingress 2.0.2 as a developer preview. The 2.X family introduces a number of changes to allow Emissary-ingress to more gracefully handle larger installations, reduce global configuration to better handle multitenant or multiorganizational installations, reduce memory footprint, and improve performance. We welcome feedback!! Join us on Slack and let us know what you think.
Envoy security updates
Upgraded envoy to 1.17.4 to address security vulnerabilities CVE-2021-32777, CVE-2021-32778, CVE-2021-32779, and CVE-2021-32781.
Expose Envoy's allow_chunked_length HTTPProtocolOption
You can now set
allow_chunked_length in the Ambassador Module to configure the same value in Envoy.Envoy-configuration snapshots saved
Envoy-configuration snapshots get saved (as
ambex-#.json) in /ambassador/snapshots. The number of snapshots is controlled by the AMBASSADOR_AMBEX_SNAPSHOT_COUNT environment variable; set it to 0 to disable. The default is 30.Version 2.0.1-ea (August 12, 2021)
Developer Preview!
We're pleased to introduce Emissary-ingress 2.0.1 as a developer preview. The 2.X family introduces a number of changes to allow Emissary-ingress to more gracefully handle larger installations, reduce global configuration to better handle multitenant or multiorganizational installations, reduce memory footprint, and improve performance. We welcome feedback!! Join us on Slack and let us know what you think.
Improved Ambassador Cloud visibility
Ambassador Agent reports sidecar process information and
AmbassadorMapping OpenAPI documentation to Ambassador Cloud to provide more visibility into services and clusters.Configurable per-AmbassadorListener statistics prefix
The optional
stats_prefix element of the AmbassadorListener CRD now determines the prefix of HTTP statistics emitted for a specific AmbassadorListener.Configurable statistics names
The optional
stats_name element of AmbassadorMapping, AmbassadorTCPMapping, AuthService, LogService, RateLimitService, and TracingService now sets the name under which cluster statistics will be logged. The default is the service, with non-alphanumeric characters replaced by underscores.Updated klog to reduce log noise
We have updated to
k8s.io/klog/v2 to track upstream and to quiet unnecessary log output.Subsecond time resolution in logs
Logs now include subsecond time resolutions, rather than just seconds.
Configurable Envoy-configuration rate limiting
Set
AMBASSADOR_AMBEX_NO_RATELIMIT to true to completely disable ratelimiting Envoy reconfiguration under memory pressure. This can help performance with the endpoint or Consul resolvers, but could make OOMkills more likely with large configurations. The default is false, meaning that the rate limiter is active.Version 2.0.0-ea (June 24, 2021)
Developer Preview!
We're pleased to introduce Emissary-ingress 2.0.0 as a developer preview. The 2.X family introduces a number of changes to allow Emissary-ingress to more gracefully handle larger installations, reduce global configuration to better handle multitenant or multiorganizational installations, reduce memory footprint, and improve performance. We welcome feedback!! Join us on Slack and let us know what you think.
Feature: Configuration API v3alpha1
Emissary-ingress 2.0.0 introduces API version
x.getambassador.io/v3alpha1 for configuration changes that are not backwards compatible with the 1.X family. API versions getambassador.io/v0, getambassador.io/v1, and getambassador.io/v2 are deprecated. Further details are available in the 2.0.0 Changes document.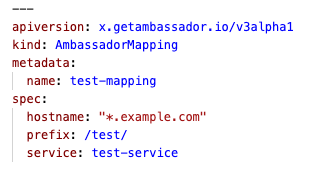

Feature: The AmbassadorListener Resource
The new
AmbassadorListener CRD defines where and how to listen for requests from the network, and which AmbassadorHost definitions should be used to process those requests. Note that the AmbassadorListener CRD is mandatory and consolidates all port configuration; see the AmbassadorListener documentation for more details.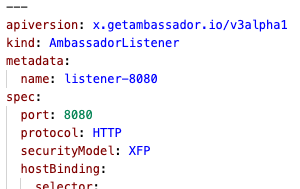

AmbassadorMapping hostname DNS glob support
Where
AmbassadorMapping's host field is either an exact match or (with host_regex set) a regex, the new hostname element is always a DNS glob. Use hostname instead of host for best results.Feature: Memory usage improvements for installations with many AmbassadorHosts
The behavior of the Ambassador module
prune_unreachable_routes field is now automatic, which should reduce Envoy memory requirements for installations with many AmbassadorHosts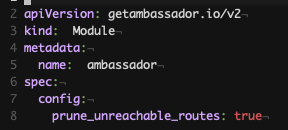

Bug Fix: Independent Host actions supported
Each
AmbassadorHost can specify its requestPolicy.insecure.action independently of any other AmbassadorHost, allowing for HTTP routing as flexible as HTTPS routing.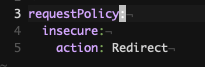

Bug Fix: Correctly set Ingress resource status in all cases
Emissary-ingress 2.0.0 fixes a regression in detecting the Ambassador Kubernetes service that could cause the wrong IP or hostname to be used in Ingress statuses -- thanks, Noah Fontes!

Stricter mTLS enforcement
Emissary-ingress 2.0.0 fixes a bug where mTLS could use the wrong configuration when SNI and the
:authority header didn't matchPort configuration outside AmbassadorListener has been moved to AmbassadorListener
The
TLSContext redirect_cleartext_from and AmbassadorHost requestPolicy.insecure.additionalPort elements are no longer supported. Use a AmbassadorListener for this functionality instead.PROXY protocol configuration has been moved to AmbassadorListener
The
use_proxy_protocol element of the Ambassador Module is no longer supported, as it is now part of the AmbassadorListener resource (and can be set per-AmbassadorListener rather than globally).Stricter rules for AmbassadorHost/AmbassadorMapping association
An
AmbassadorMapping will only be matched with an AmbassadorHost if the AmbassadorMapping's host or the AmbassadorHost's selector (or both) are explicitly set, and match. This change can significantly improve Emissary-ingress's memory footprint when many AmbassadorHosts are involved. Further details are available in the 2.0.0 Changes document.Change: AmbassadorHost or Ingress now required for TLS termination
An
AmbassadorHost or Ingress resource is now required when terminating TLS -- simply creating a TLSContext is not sufficient. Further details are available in the AmbassadorHost CRD documentation.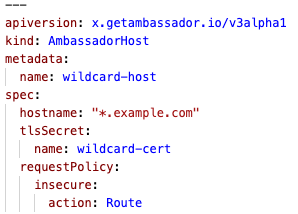

Envoy V3 APIs
By default, Emissary-ingress will configure Envoy using the V3 Envoy API. This change is mostly transparent to users, but note that Envoy V3 does not support unsafe regular expressions or, e.g., Zipkin's V1 collector protocol. Further details are available in the 2.0.0 Changes document.
Change: Module-based TLS no longer supported
The
tls module and the tls field in the Ambassador module are no longer supported. Please use TLSContext resources instead.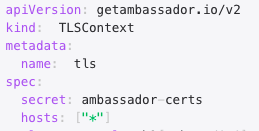

Higher performance while generating Envoy configuration now enabled by default
The environment variable
AMBASSADOR_FAST_RECONFIGURE is now set by default, enabling the higher-performance implementation of the code that Emissary-ingress uses to generate and validate Envoy configurations.Service Preview no longer supported
Service Preview and the
AGENT_SERVICE environment variable are no longer supported. The Telepresence product replaces this functionality.edgectl no longer supported
The
edgectl CLI tool has been deprecated; please use the emissary-ingress helm chart instead.Version 1.14.3 (February 25, 2022)
Envoy security updates
Upgraded Envoy to address security vulnerabilities CVE-2021-43824, CVE-2021-43825, CVE-2021-43826, CVE-2022-21654, and CVE-2022-21655.
Version 1.14.2 (September 29, 2021)
Mappings support controlling DNS refresh with DNS TTL
You can now set
respect_dns_ttl in Ambassador Mappings. When true it configures that upstream's refresh rate to be set to resource record’s TTLMappings support configuring strict or logical DNS
You can now set
dns_type in Ambassador Mappings to use Envoy's logical_dns resolution instead of the default strict_dns.Support configuring upstream buffer size
You can now set
buffer_limit_bytes in the ambassador Module to to change the size of the upstream read and write buffers. The default is 1MiB.Version 1.14.1 (August 24, 2021)
Envoy security updates
Upgraded Envoy to 1.17.4 to address security vulnerabilities CVE-2021-32777, CVE-2021-32778, CVE-2021-32779, and CVE-2021-32781.
Version 1.14.0 (August 19, 2021)
Envoy upgraded to 1.17.3!
Update from Envoy 1.15 to 1.17.3
Expose Envoy's allow_chunked_length HTTPProtocolOption
You can now set
allow_chunked_length in the Ambassador Module to configure the same value in Envoy.Default Envoy API version is now V3
AMBASSADOR_ENVOY_API_VERSION now defaults to V3Subsecond time resolution in logs
Logs now include subsecond time resolutions, rather than just seconds.
Version 1.13.10 (July 28, 2021)
Bug Fix: Fix for CORS origins configuration on the Mapping resource
Fixed a regression when specifying a comma separated string for
cors.origins on the Mapping resource. ([#3609](https://github.com/emissary-ingress/emissary/issues/3609))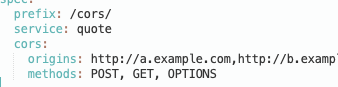

New Envoy-configuration snapshots for debugging
Envoy-configuration snapshots get saved (as
ambex-#.json) in /ambassador/snapshots. The number of snapshots is controlled by the AMBASSADOR_AMBEX_SNAPSHOT_COUNT environment variable; set it to 0 to disable. The default is 30.Optionally remove ratelimiting for Envoy reconfiguration
Set
AMBASSADOR_AMBEX_NO_RATELIMIT to true to completely disable ratelimiting Envoy reconfiguration under memory pressure. This can help performance with the endpoint or Consul resolvers, but could make OOMkills more likely with large configurations. The default is false, meaning that the rate limiter is active.Version 1.13.9 (June 30, 2021)
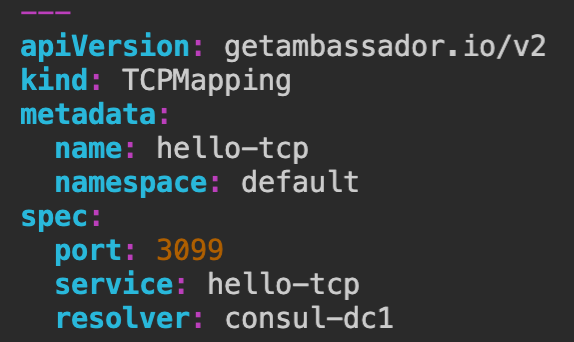
Fix for TCPMappings
Configuring multiple TCPMappings with the same ports (but different hosts) no longer generates invalid Envoy configuration.
Version 1.13.8 (June 08, 2021)
Bug Fix: Fix Ambassador Cloud Service Details
Ambassador Agent now accurately reports up-to-date Endpoint information to Ambassador Cloud

Improved Argo Rollouts Experience with Ambassador Cloud
Ambassador Agent reports ConfigMaps and Deployments to Ambassador Cloud to provide a better Argo Rollouts experience. See [Argo+Ambassador documentation](https://www.getambassador.io/docs/argo) for more info.
Version 1.13.7 (June 03, 2021)
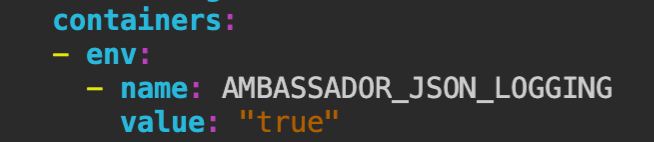
Feature: JSON logging support
Add AMBASSADOR_JSON_LOGGING to enable JSON for most of the Ambassador control plane. Some (but few) logs from gunicorn and the Kubernetes client-go package still log text.

Bug Fix: Consul resolver bugfix with TCPMappings
Fixed a bug where the Consul resolver would not actually use Consul endpoints with TCPMappings.

Change: Memory usage calculation improvements
Ambassador now calculates its own memory usage in a way that is more similar to how the kernel OOMKiller tracks memory.
Version 1.13.6 (May 24, 2021)
Quieter logs in legacy mode
Fixed a regression where Ambassador snapshot data was logged at the INFO label when using
AMBASSADOR_LEGACY_MODE=true.Version 1.13.5 (May 13, 2021)
Correctly support proper_case and preserve_external_request_id
Fix a regression from 1.8.0 that prevented
ambassador Module config keys proper_case and preserve_external_request_id from working correctly.Correctly support Ingress statuses in all cases
Fixed a regression in detecting the Ambassador Kubernetes service that could cause the wrong IP or hostname to be used in Ingress statuses (thanks, [Noah Fontes](https://github.com/impl)!
Version 1.13.4 (May 11, 2021)
Security Update: Envoy 1.15.5
Incorporate the Envoy 1.15.5 security update by adding the
reject_requests_with_escaped_slashes option to the Ambassador module.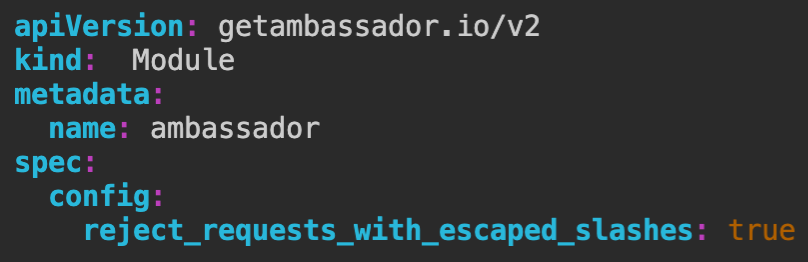

For a detailed list of all the changes in past releases, please consult the CHANGELOG.








